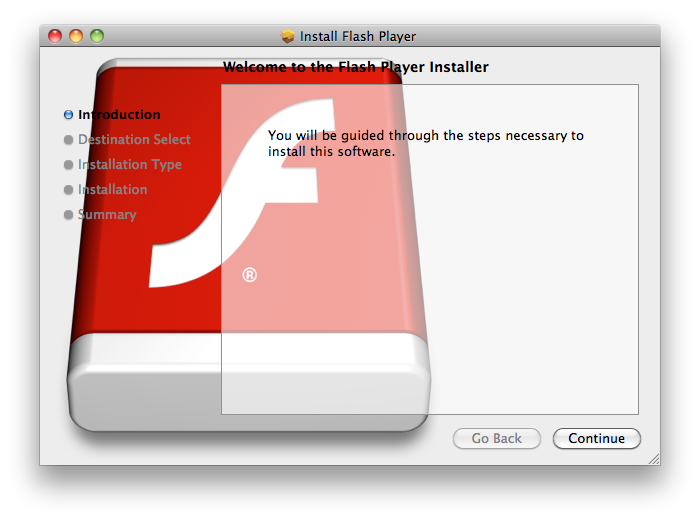
A few months ago security company F-Secure that posed as an installer application for Adobe Flash, taking advantage of the popularity of the plug-in to trick users into installing it. After installation, the Trojan would alter the system's hosts file to redirect Google sites to fraudulent servers. Now a new Trojan for OS X that does pretty much the same thing: masquerades as a Flash Player installer to trick people into installing the program. Unlike the previous Flash Trojan (called Bash/QHost.WB), which changed one file on the system, this new Trojan is a bit more complex and first deactivates network security features, then installs a dyld library that will run and inject code into applications that the user is running. The Trojan will also try to send personal information and machine-specific information to remote servers. The Flashback Trojan's installer looks like a legitimate program.
Intego Intego calls the Trojan OSX/flashback.A, and is not too specific about how this Trojan runs, but it will undoubtedly compromise your system if you run it. The Trojan appears to use Apple's basic installer package system and includes Flash player logos so it looks like a legitimate software package. While people may be concerned about this Trojan and other, the risk of being infected is exceptionally low.
If you need Adobe Flash on your system, just go to and get it or go to a trusted source like CNET's. Doing this will ensure that you get the file directly as the developer intended, as opposed to using either an outdated version, a modified version, or a rogue application disguised as a Flash installer. In addition to being easy to avoid, the Flashback Trojan does not self-replicate so it will not affect other systems. In essence, as with all Trojan attacks this is an attempt to disguise malicious software in hopes of stealing information from unsuspecting people.
Adobe's real Flash installer looks like this when run, has a Flash player icon, and is distributed in a disk image. Origin sims 3 island paradise download for mac. Intego claims its VirusBarrier X6 anti-malware utility can detect and remove this latest Trojan if it is installed, but other scanners should soon also be updated to detect this threat. While there is no information on how to manually remove Flashback, Intego says the program installs its malicious dynamic library in the /username/Library/Preferences/ folder as the file 'Preferences.dyld,' so you can go to that location and remove that file to dispose of the code. Besides getting your download updates and installers from trusted sources, you can do some additional things to protect your system from these and other threats:.
Turn off Safari's auto-open command In Safari, go to the General section of the preferences and uncheck the option to 'Open safe files after downloading.' While this will not open applications, if checked it will open documents and media that may contain executable code, and turning it off is recommended. Install a malware scanner Install a scanner like Sophos, VirusBarrier, ClamXav, Kaspersky, or iAntiVirus, and set it up to scan your e-mail and your download folders. While doing this will help ensure your downloads are safe, the rarity of malware threats on OS X makes it optional. Nevertheless, this has steadily become more of a recommendation of mine.
Never trust a program If something asks you to install an item on your system, shut it down and confirm the source of the item. Only install programs on your system if you know exactly where they came from.
Fake Flash Player trojan installer While things have been relatively quiet on the malware front for OS X since a on Russian payment processing firm ChronoPay appeared to have taken down MacDefender nearly two months ago, one new trojan horse did pop up earlier this month. As, the trojan known as 'OSX.QHost.WB.A' masquerades as a Flash Player installer but actually adds entries to a computer's hosts file to redirect users attempting to visit certain Google sites. Once installed, the trojan adds entries to the hosts file to hijack users visiting various Google sites (e.g., Google.com.tw, Google.com.tl, et cetera) to the IP address 91.224.160.26, which is located in Netherlands.
The server at the IP address displays a fake webpage designed to appear similar to the legitimate Google site.Search results on the fake Google pages actually lead to pop-up windows that load external content which was broken at the time of discovery but presumably consisted of advertisements of some sort. While the threat as implemented at the time of discovery was relatively mild, inexperienced users falling for the trojan could find themselves unaware of what had happened to their systems and how to fix the hijacked routing added by the malware. Consequently, Apple earlier this week made its first significant addition to its 'XProtect.plist' file since the spate of MacDefender variants surfaced in June. The XProtect.plist file contains malware definitions to enable users' systems to recognize and warn users of malicious downloads, a feature that with Mac OS X Snow Leopard back in 2009. The original anti-malware system required manual updates to account for new threats, and as such was updated only rarely by Apple as part of larger software updates. But with an Apple issued in response to the MacDefender threat earlier this year, Mac OS X systems are now able to make for updates to that file to ensure up-to-date protection against malware.
No, it's not a 'virus'. It's a trojan. You think it's good, but its bad. Depending on if you think 'flash' is 'good').
A question I have though, is under what conditions should ANY software modify the hosts file? Should Apple even allow programs that have been granted administrative rights to alter the hosts file? There is only a very limited benvolent use case for such an action, and that very related to what they did here: some anti-ad or anti-spyware utilities modify a host file to redirect known ad-producing domains to a 'safe' domain. I personally think any modification of the host file should be given a warning like this: The program is trying to update a core Mac OS X system file that is used to provide network connectivity. While online advertisement blocking programs may require legitimate use of this file, most others applications may represent an attempt to install malicious software onto your computer.

Are you sure you want to allow program to modify this file? So this trojan, doesn't prompt you like a normal update correct? Cause there was a normal update for flash that was found threw software update. Or was that the trojan? The reason i ask is because I'm new to mac and I assumed that if i was able to find the update threw the software updater that it was safe.
Or is this trojan just like a pc virus/malware where it will try and install after clicking a bad link or going to a bad site? Software Update won't include updates for non-Apple apps. If you get the update notice from already installed software, that should be safe. If, however, you visit a website, like I did this morning, that says you need an updated version of Flash player, don't install it there. Instead, go to Adobe's site directly and download and install the player.
To download Flash player: To find your currently installed version: http://www.adobe.com/software/flash/about/. Its totally fine.
Avoid The Latest Fake Flash Player Installer For Mac Mac
Just a Jailbreak program on his computer backing up his Cydia blobs I think.could be wrong No, you are quite right, it's the firmware signing address for iPhones. This is completely inert, nothing to see there. AidenShaw is simply demonstrating a lack of knowledge and basic research skills. If this is not enough, check on the website that AidenShaw posted (www.saurik.com/id/12), and read why the address is in the hosts file. Seeing as the original server is gone, no one has anything to worry about. Macrumours should really update the article to reflect that.

